21 | Add to Reading ListSource URL: eprint.iacr.org- Date: 2016-05-09 21:22:18
|
|---|
22 | Add to Reading ListSource URL: theory.stanford.edu- Date: 2010-03-09 22:02:41
|
|---|
23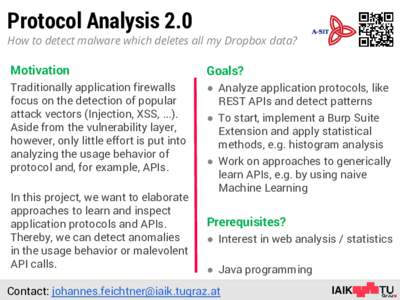 | Add to Reading ListSource URL: www.iaik.tugraz.at- Date: 2015-12-01 06:00:06
|
|---|
24 | Add to Reading ListSource URL: www.prisma-statement.org- Date: 2016-01-07 14:14:41
|
|---|
25 | Add to Reading ListSource URL: europa.informatik.uni-freiburg.deLanguage: English - Date: 2012-03-01 02:59:53
|
|---|
26 | Add to Reading ListSource URL: www.rvs.uni-bielefeld.deLanguage: English - Date: 2005-06-15 07:43:48
|
|---|
27 | Add to Reading ListSource URL: users.ece.cmu.eduLanguage: English - Date: 2014-05-29 15:38:01
|
|---|
28 | Add to Reading ListSource URL: cs-www.cs.yale.eduLanguage: English - Date: 2006-09-25 10:55:42
|
|---|
29 | Add to Reading ListSource URL: www.prisma-statement.orgLanguage: English - Date: 2015-10-20 11:28:22
|
|---|
30 | Add to Reading ListSource URL: www.curee.orgLanguage: English - Date: 2006-09-08 21:51:14
|
|---|